A Brief Guide to AWS IAM Policy Types and Use Cases
How to Effectively Manage User Permissions and Access Controls in AWS
IAM
Identity and Access Management (IAM) policies are essential tools for managing access to your organization's resources in Amazon Web Services (AWS). IAM policies are written in a standardized policy language and can be used to authenticate and authorize API service calls.
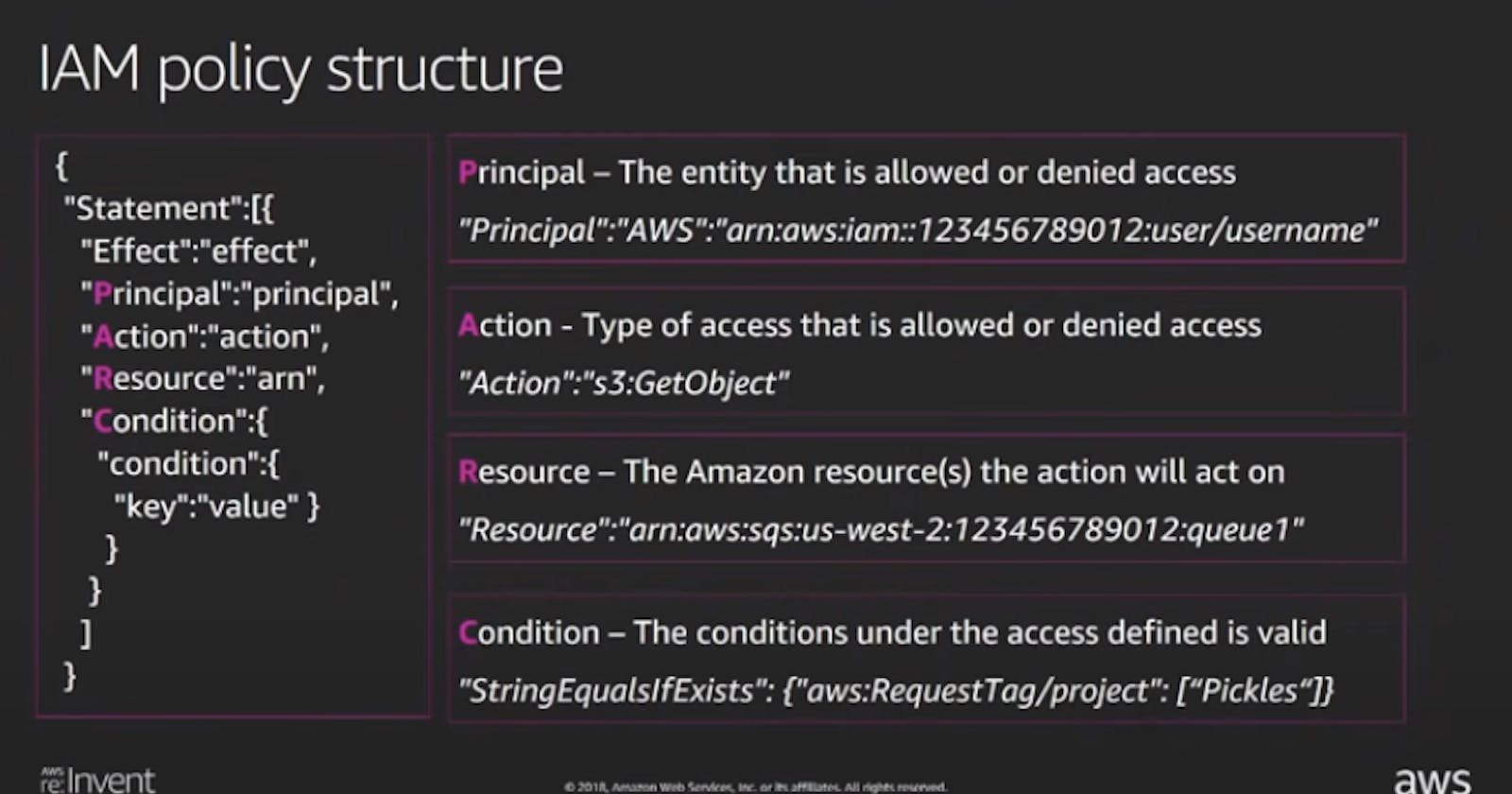
IAM Policy Structure
There are two aspects to IAM policy:
Specification: Defining access policies
Enforcement: Evaluating policies
When we define access policies, we specify which IAM principles are allowed to perform which actions on specific AWS resources and under which conditions. IAM enforces this access by evaluating the AWS requests and the policies you defined and returns either yes or no.
IAM Policy Evaluation
Whenever we are debugging an IAM policy that why a certain policy is getting denied or accepted, we must check that what is not MATCHING. It all boils down to matching Action, Resource, or Condition from the Context of AWS API call to what is defined in POLICY.
During authorization, the AWS enforcement code uses values from the request context to check for matching policies and determine whether to allow or deny the request.
AWS checks each policy that applies to the context of the request. If a single policy denies the request, AWS denies the entire request and stops evaluating policies. This is called an explicit deny. Because requests are denied by default, IAM authorizes your request only if every part of your request is allowed by the applicable policies. The evaluation logic for a request within a single account follows these rules:
By default, all requests are implicitly denied. (Alternatively, by default, the AWS account root user has full access.)
An explicit allow in an identity-based or resource-based policy overrides this default.
If a permissions boundary, Organizations SCP, or session policy is present, it might override the allow with an implicit deny.
An explicit deny in any policy overrides any allows.
After your request has been authenticated and authorized, AWS approves the request. If you need to make a request in a different account, a policy in the other account must allow you to access the resource. In addition, the IAM entity that you use to make the request must have an identity-based policy that allows the request.

IAM Policy Types
There are several types of IAM policies, each designed for specific use cases. By using these different types of IAM policies, organizations can effectively manage their resources and secure their valuable assets. However, it is essential to understand which policy type is best suited for a specific use case and to use them in conjunction with other security best practices. The most common types of IAM policies are:
Service Control Policies (SCP): These policies are used to apply guardrails and limit access to AWS services at the AWS Organizations level. By default, all resources are allowed, and access to accounts is restricted using deny statements.
Permission Policies and Permission Boundaries: These policies provide granular permissions control over IAM principles and allow organizations to set maximum permissions for these principles. Permission policies are used to grant permissions to create and provision resources, while permission boundaries limit the maximum set of permissions a principal can access. These policies can also be used to allow or deny access to resources based on specific regions using the RequestedRegion condition.
Scoped Down Policies: These policies are used to further reduce generally shared permissions when assuming a particular role at the AWS Security Token Service (STS) level.
Resource-Based Policies: These policies are used for cross-account access and control access from resources at specific AWS services such as S3 Bucket Policy. Resource-based policies are applied directly to the resource that needs to be shared, rather than using a role as a proxy. These policies specify which principal can access the resource, including accounts, IAM users, federated users, IAM roles, assumed-role sessions, or AWS services.
Endpoint Policies: These policies are used to control access to a service through a specific VPC endpoint and are applied at the VPC endpoint level.
Conclusion
Remember, the use of IAM policies is just one aspect of AWS security. Be sure to implement other security best practices, such as regularly reviewing access permissions and using multi-factor authentication (MFA) to further enhance the security of your organization's resources.
Share your experience with IAM policies and how you have utilized them in your organization. Have you found a particular policy type to be more useful than others? Have you implemented IAM policies for other use cases? Please contribute to the ongoing conversation on IAM policy management and security best practices.